安洵杯-MISC

安洵杯-MISC
1.打开文件Signal一串二进制数据
1 | from Crypto.Util.number import * |
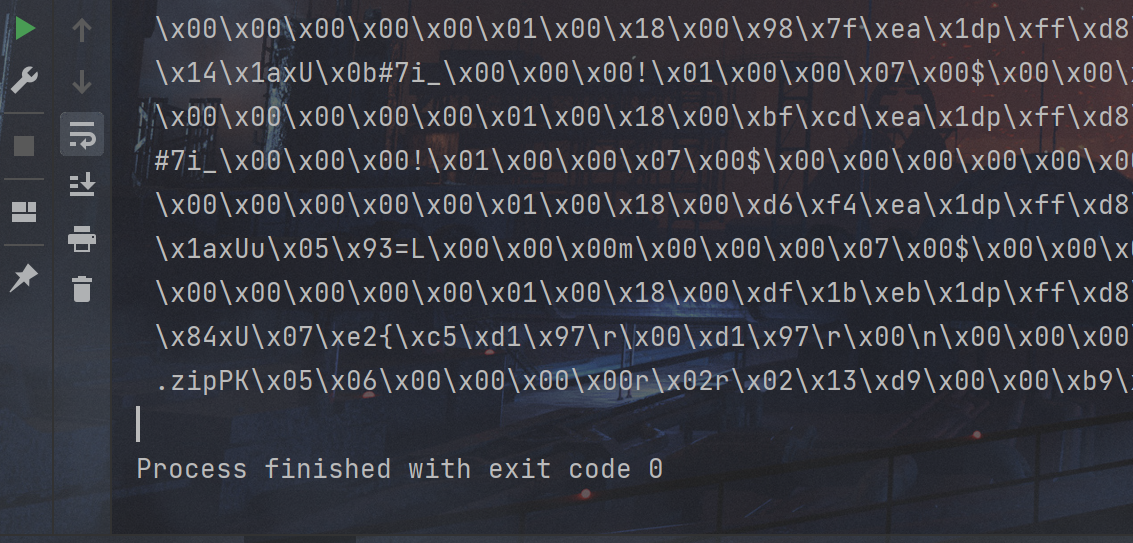
发现PK压缩包标志
1 | from Crypto.Util.number import * |
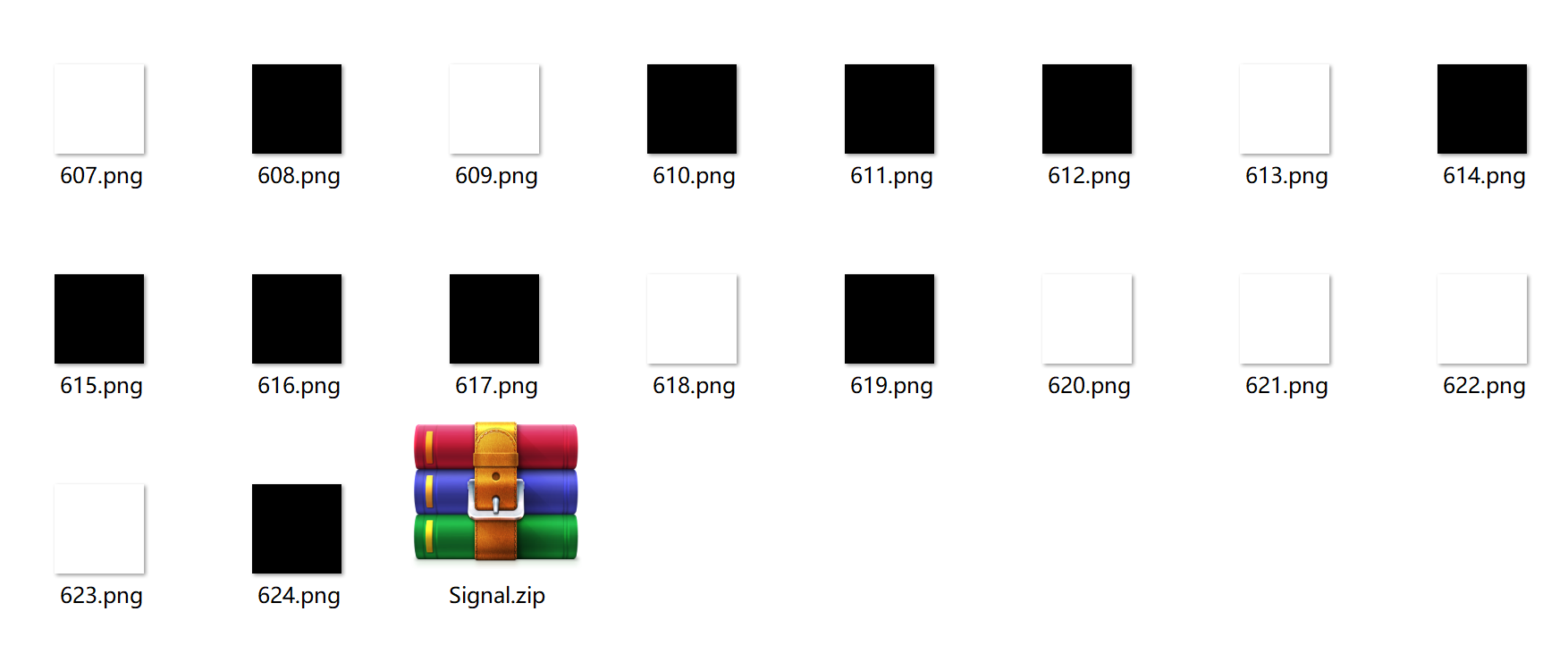
2.压缩包里是625张黑和白的图片,以及一个加密的压缩包
1 | from PIL import Image |

得到解压密码
1 | 187J3X1&DX3906@! |
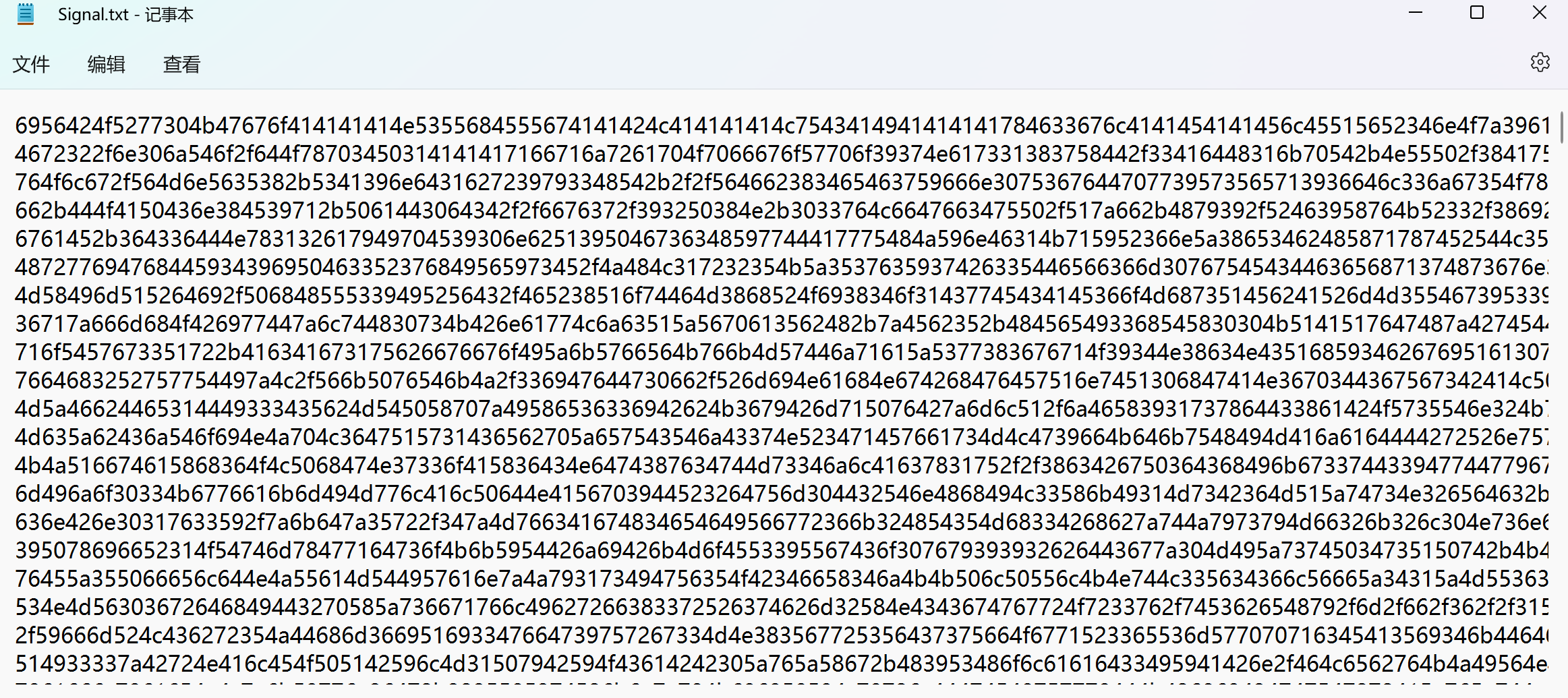
3.压缩包里是一串16进制数据
放到CyberChef里解码https://cyberchef.org/
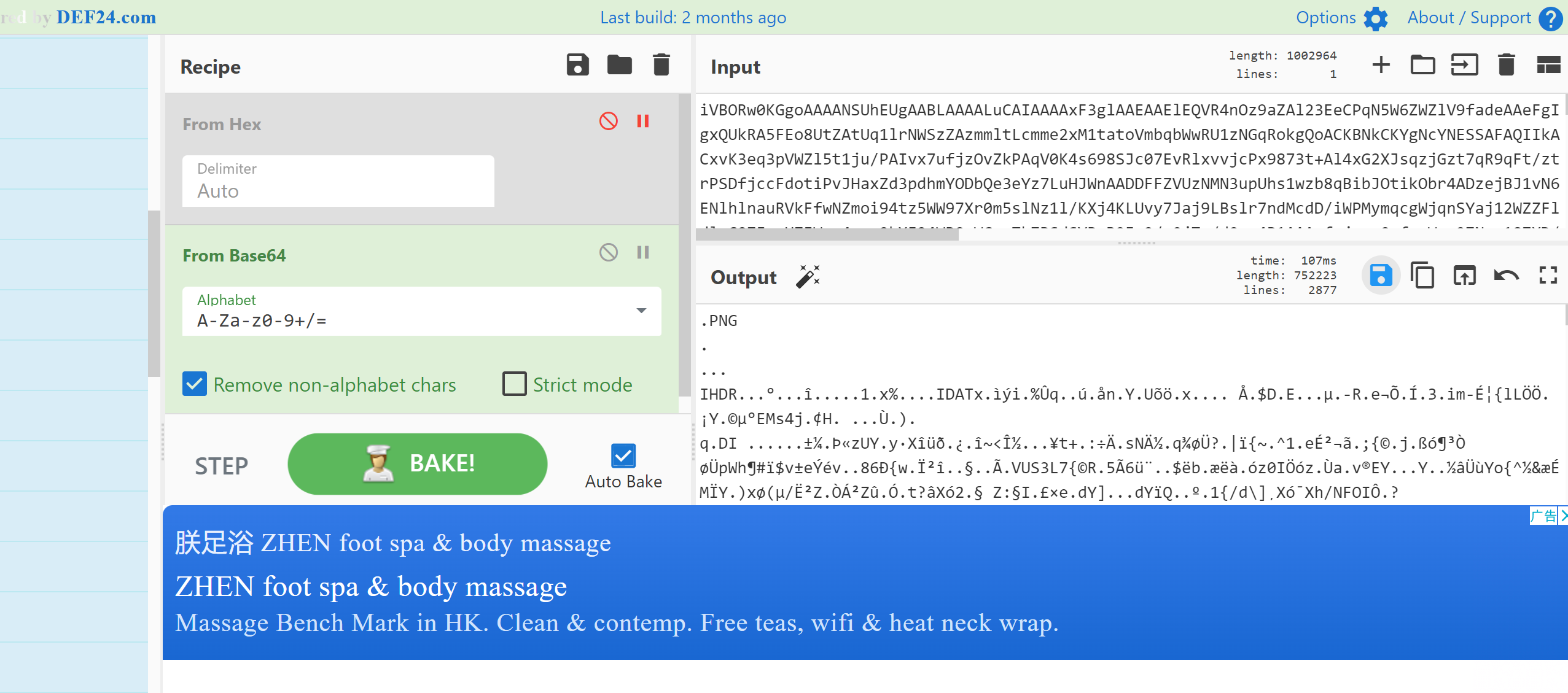
保存为png图片 得到

4.图片用stegosolve打开,通道全选发现flag
5.结语:
1.二进制数据转换为字节数据,发现是压缩包
2.压缩包里625张图片组装生成二维码,得到里面压缩包密码
3.解开压缩包里面有16进制文本数据得到base64数据,再解码得到png数据,保存png
4.png图片用stegosolve打开通道全选能够发现flag
题目文件放到里云盘需要自提
Signal https://www.aliyundrive.com/s/eKRAdp3chp6 提取码: x23v 点击链接保存,或者复制本段内容,打开「阿里云盘」APP ,无需下载极速在线查看,视频原画倍速播放。
Comments